How to Seamlessly Connect a VPC to Your Lambda Function
Read Time 6 mins | Written by: Kenneth Hough

In the ever-evolving landscape of cloud computing, AWS Lambda functions have revolutionized how we approach serverless architecture, offering unparalleled flexibility and scalability. However, there are instances when the simplicity of an AWS Lambda function encounters a hurdle: the need to access resources residing within a Virtual Private Cloud (VPC). Picture this: your Lambda function requires interaction with private databases like RDS or specific EC2 instances shielded within a secured network. While various solutions exist for Lambda function execution, a particular design implementation may necessitate direct access to these private resources within the VPC, where other alternatives fall short or lack applicability.
This intersection between AWS Lambda and VPCs unlocks a world of possibilities, enabling a secure and direct channel for your serverless functions to interact with private resources. Let's explore why this integration is a crucial piece of the puzzle and how it empowers specific design implementations that demand direct and secure access within a VPC's protected enclave.
Let's dive in to see how we can connect a AWS Lambda to a VPC!
Security Groups
When integrating an AWS Lambda function with a VPC, it is essential to have a dedicated security group attached to the function. This security group acts as a gatekeeper, allowing us to control access to various resources within the VPC. By carefully defining inbound and outbound connections, we can establish strict permissions and restrictions. For instance, if we want to limit access to a specific RDS database, we can simply add an inbound rule to the RDS security group, allowing only database traffic from the security group associated with the Lambda function. This ensures a secure and controlled environment for seamless communication between our serverless function and private resources.
To begin securing your AWS Lambda function within a VPC, simply log in to your AWS console and navigate to the Security Group section. You can easily access this section either from the EC2 service console by finding the Network & Security option in the left sidebar, or from the VPC console by selecting the Security option in the left sidebar. Once you're on the security group page, click on the Create security group button.
When creating a security group for your AWS Lambda function within a VPC, it is crucial to provide a clear and descriptive explanation of its purpose. For instance, in the screenshot below, I specify that this security group is intended to allow my Lambda function to access an RDS instance. By providing a concise and informative name, as well as a brief explanation, you can effectively manage your security groups and ensure that you are adhering to best practices. This not only enhances the organization and clarity of your infrastructure, but also maximizes the security and efficiency of your serverless functions within the VPC environment.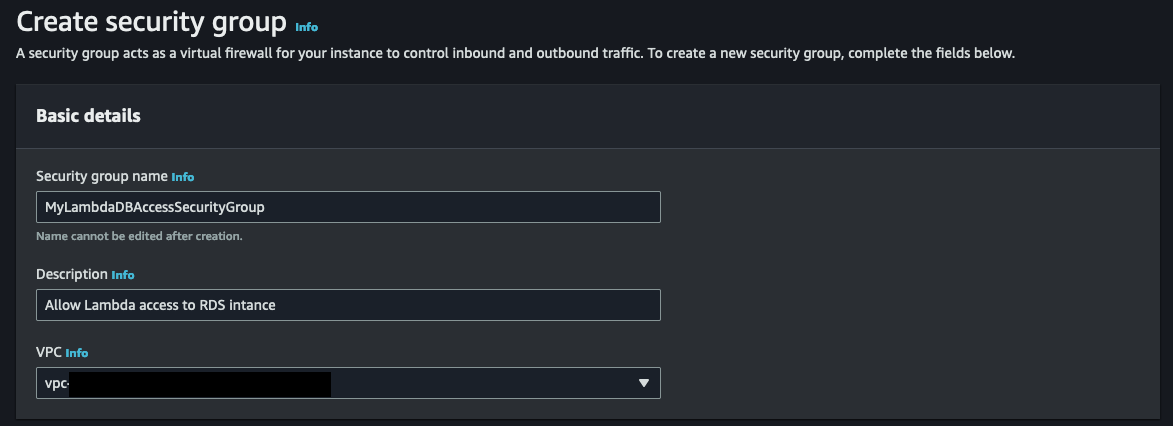
Now it's time to establish the rules for inbound and outbound connections in our AWS Lambda function. In this case, we don't need to set any inbound rules since there won't be any connections made to the Lambda function. However, for outbound rules, I've chosen to keep the default rule that allows any traffic to exit the Lambda function. But if you want to enhance security even further, you can specify which protocol is allowed. For example, in my scenario with the RDS database, I might specify the MySql/Aurora protocol and the security group associated with my RDS.
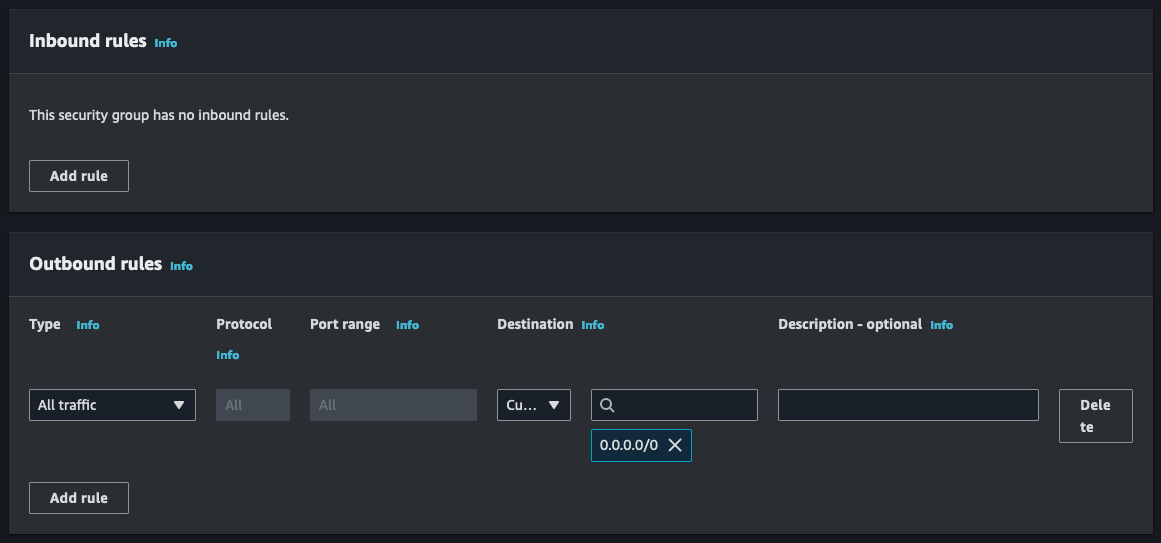
Now that we have our security group created, we will next update our Lambda function role to include required permissions to connect to a VPC.
Execution Roles and Permissions
To establish a successful connection between your AWS Lambda function and a VPC, it's essential to equip the role attached to the Lambda function with permissions to create the necessary network interface to communicate inside the VPC.
The required permissions include:
- ec2:CreateNetworkInterface
- ec2:DescribeNetworkInterfaces
- ec2:DeleteNetworkInterface
- ec2:AssignPrivateIpAddresses
- ec2:UnassignPrivateIpAddresses
These permissions are conveniently bundled in the AWS managed policy called AWSLambdaVPCAccessExecutionRole. It's important to note that these permissions are only necessary for the creation of ENIs, not for invoking your VPC function. In other words, even if you remove these permissions from your execution role, you can still successfully invoke your VPC function.
For more comprehensive details on execution roles and permissions, you can refer to the AWS Developer Guide.
To incorporate the necessary execution role, we must modify the current execution role that is linked to your Lambda function. This can be achieved by accessing the IAM service console and locating the specific role associated with your lambda function. Alternatively, you can navigate to your Lambda function and choose Permissions in the Configuration tab. Clicking on the role name will open a new tab or window displaying the IAM role. See screenshot below: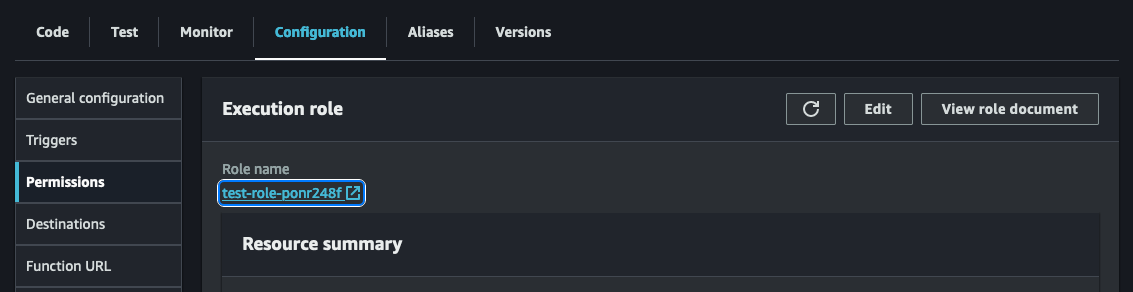
Once you have the IAM role for your Lambda function open, we will need to attach a new policy. Click on the Add permissions drop-down and then Attach policies.

Search for the AWSLambdaVPCExecution role and add the permission to your role.
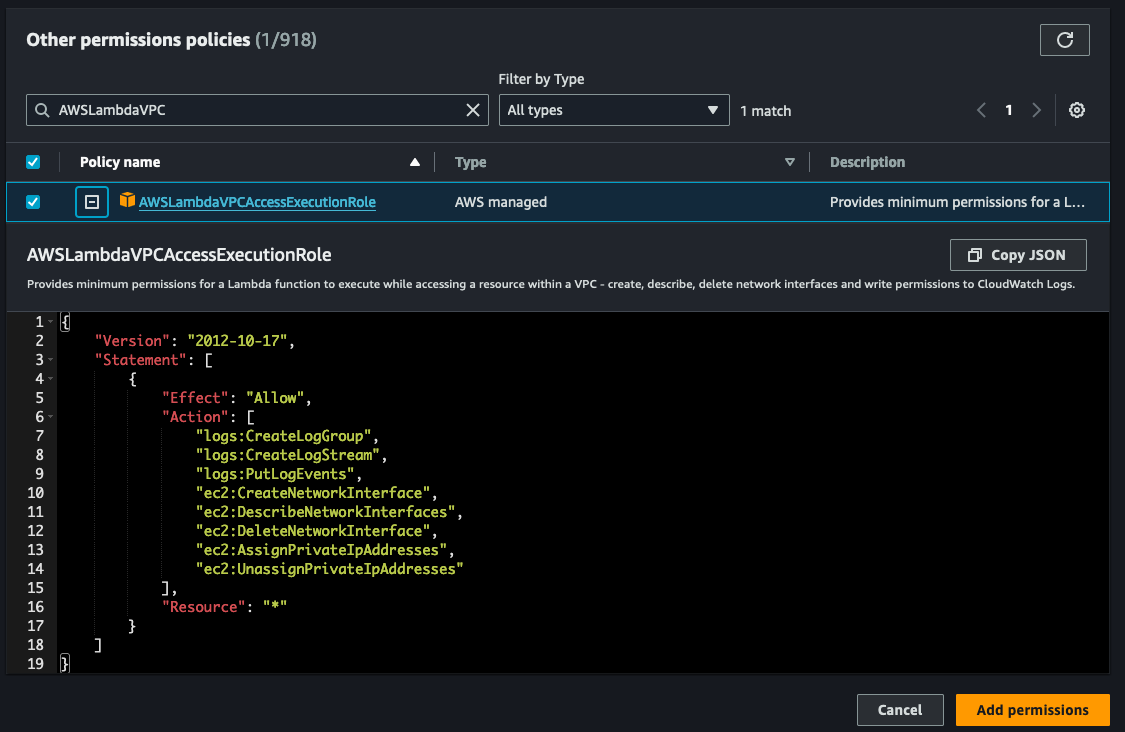
And with that, you're ready to connect your AWS Lambda function to a VPC!
Attaching an Lambda Function to a VPC
Now, as we reach the culmination of our journey, it's time to connect your Lambda function to a VPC. To accomplish this, simply navigate to your Lambda function and open the Configurations tab. Look for the VPC option on the left sidebar, as depicted in the screenshot below.
To edit the VPC configuration for your lambda, click on the 'Edit' button.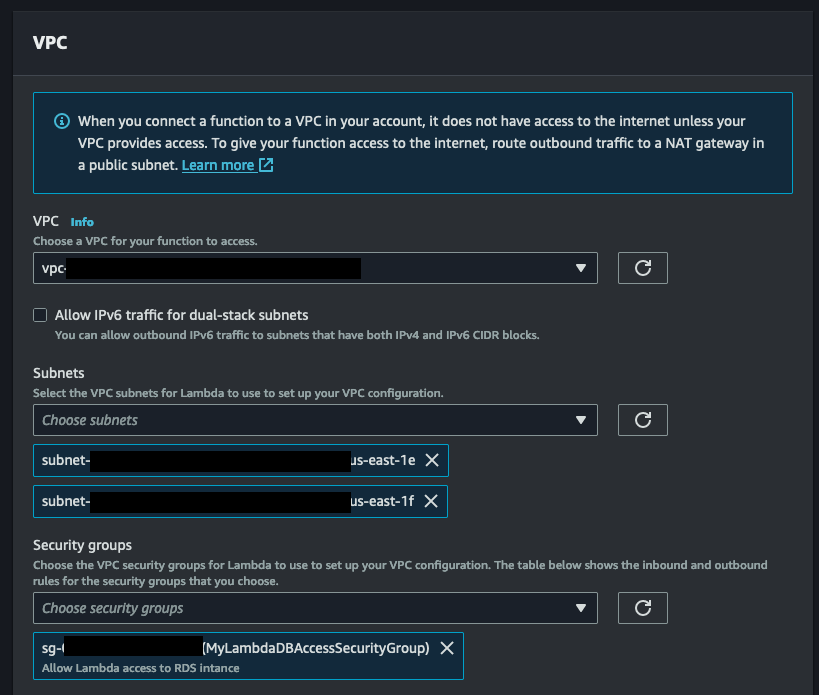
Once you've reached the Edit VPC page, it's time to choose the VPC that will be the home for your Lambda function. Next, carefully select the subnets where your function will operate within the VPC. To ensure high availability, a minimum of 2 subnets is required. Lastly, don't forget to pick the security group you created earlier in this tutorial. After making these selections, simply click 'Save' at the bottom of the page. Keep in mind that the VPC configuration may take some time to update, so make sure to keep an eye on the informative blue message above before putting your function to the test.
And there you have it, my friends! A flawless integration of an AWS Lambda function with a VPC. I hope you found this tutorial enlightening and captivating, and make sure to stay tuned for more exciting AWS tutorials in the future!
Additional Considerations
Lambda Functions in a VPC Lack Internet Access by Default
Lambda functions in a VPC utilize Hyperplane ENIs to access resources within the VPC. These ENIs provide NAT capabilities, allowing connectivity from the Lambda VPC to your account VPC through VPC-to-VPC NAT (V2N). However, it's important to note that this connectivity is one-way, meaning Lambda can access resources within the VPC but lacks direct internet access.
To connect to other AWS services, you have the option to use VPC endpoints, which enable private communications between your VPC and supported AWS services. Another approach is to utilize a NAT gateway, which allows outbound traffic routing and provides internet access to Lambda functions through a public subnet.
To provide your function with internet access, you can route outbound traffic through a NAT gateway located in a public subnet. This NAT gateway has a public IP address and can establish a direct connection to the internet through the VPC's internet gateway. It's important to keep in mind that configuring a NAT gateway incurs additional costs (See below for link to NAT gateway pricing).
For more detailed information on configuring Lambda VPC networking, please refer to the following AWS Developer Guides:
A Framework Built to Accelerate App Development for Startups
Kenneth Hough
Background
I founded KeyQ in March of 2020 with the vision of helping businesses achieve the next level of success through delivering innovative and meaningful cloud solutions. Since its inception, I have worked with several businesses, non-profit organizations, and universities to design and build cloud applications that have helped streamline their business processes and reduce costs.
Prior to KeyQ, I was a medical researcher at the University of Alabama at Birmingham (UAB) in the Division of Pulmonary, Allergy, and Critical Care Medicine. UAB is also where I worked on my doctoral thesis under the mentorship of Dr. Jessy Deshane and Dr. Victor Thannickal. During my doctoral work at UAB I was exposed to the “omics” and big data, which has influenced my career choice to develop data-driven analytics platforms in the cloud.
I also have to give a big shoutout to my undergraduate education at Worcester Polytechnic Institute (WPI), where I majored in biochemistry. WPI’s motto is “Lehr und Kunst,” which roughly translates to “Theory and Practice” or “Learning and Skilled Art.” WPI truly cherishes and upholds this pedagogy, which can be seen by the teaching styles and class sizes. The learning experience I had at WPI is unique and has shaped me to be who I am, being able to learn, practice and apply.
Personal Interests
I love to learn innovative technologies and try new things. I have a broad area of interests that include serverless architectures, machine learning, artificial intelligence, bioinformatics, medical informatics, and financial technology. I am also working towards my CFA level 1 exam for 2021. Other interests and hobbies include traveling, rock climbing, rappelling, caving, camping and gardening!

